Introduction
A candidate key in DBMS is a core idea you must know. It helps keep data correct and easy to find. I will explain it in simple words. Each sentence is short and clear. You will see examples and tips I used in real projects. I worked on a school database once. I used candidate keys to fix duplicate records. This guide will show what a candidate key in DBMS means. It will compare similar terms like superkey and primary key. You will learn how to find candidate keys by hand. I will give real step steps for practice. Read on and you will feel confident about candidate key in DBMS.
What is a Candidate Key?
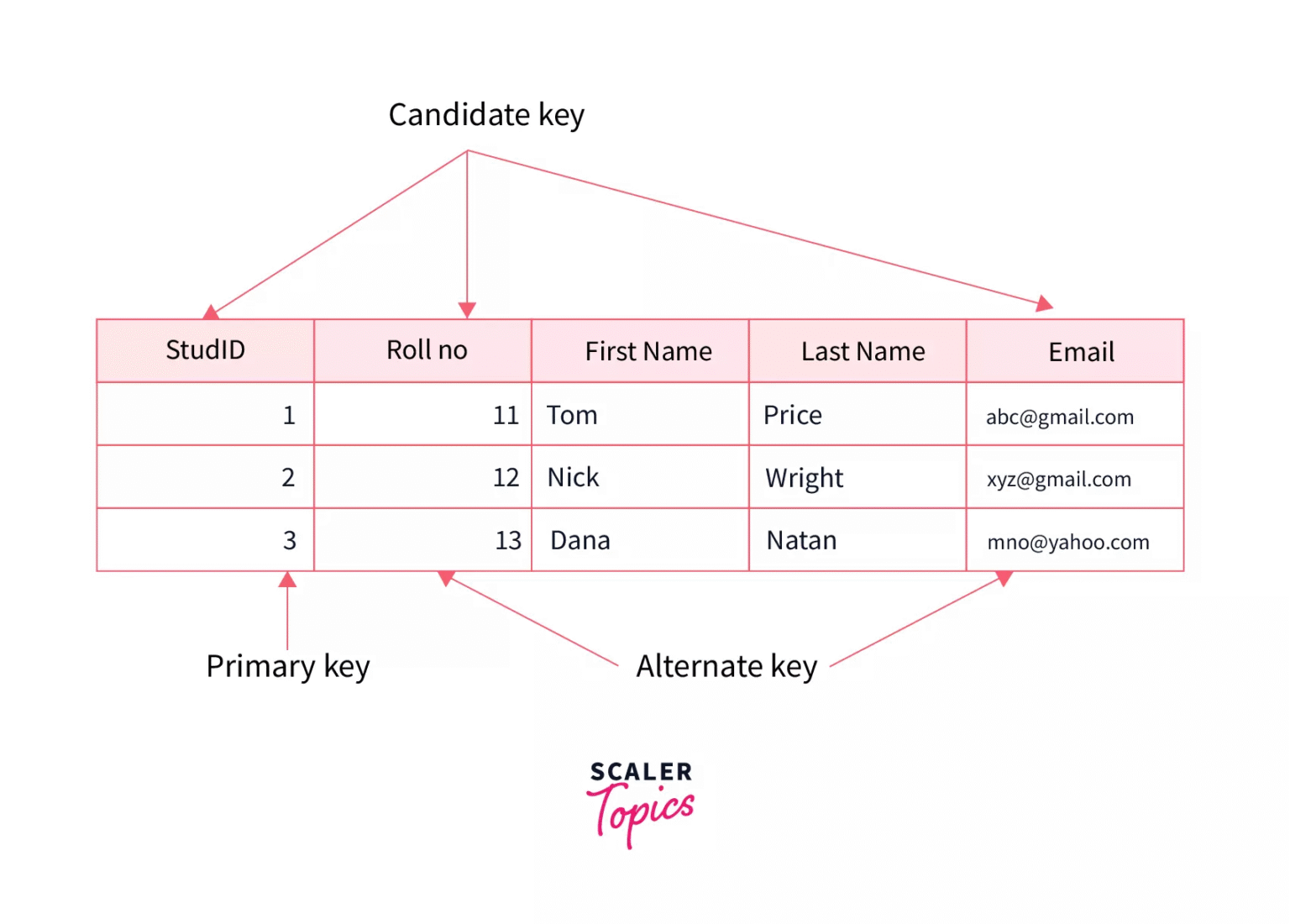
A candidate key in DBMS is an attribute set that uniquely identifies rows. It means no two rows share the same key value. A candidate key must be minimal. Minimal means no attribute can be removed and still work. Think of a student table. StudentID can be a candidate key. Email might also be a candidate key. If both work, each is a candidate key. You pick one to become the primary key. The rest remain candidate keys. Candidate keys help enforce uniqueness. They support queries and joins in a clean way. Understanding candidate key in DBMS keeps your data neat. It also helps during normalization and schema design.
Core Properties of Candidate Keys
A candidate key in DBMS has two main properties. First, it must be unique across all rows. Second, it must be minimal. Minimality avoids extra attributes in the key. If you add unnecessary attributes, the key becomes a superkey, not a candidate key. Candidate keys must not depend on other attributes for uniqueness. They must be stable over time too. A key that changes often is a bad choice. Choose attributes that remain the same. Examples include national IDs or system-generated IDs. Remember that candidate key in DBMS is both unique and minimal. These simple rules guide sound database design.
Candidate Key vs Superkey
A superkey is a set of attributes that can uniquely identify rows. A candidate key in DBMS is a special superkey. The special part is minimality. Every candidate key is a superkey. But not every superkey is a candidate key. For instance, {StudentID, Email} is a superkey. But it is not a candidate key if StudentID alone is enough. Adding attributes makes a superkey non-minimal. Think of superkeys as broad and candidate keys as narrow. Candidate key in DBMS is the smallest reliable identifier. This distinction matters when you normalize and when you enforce constraints.
Candidate Key vs Primary Key
A primary key is the chosen candidate key used to identify rows. A candidate key in DBMS is any minimal unique attribute set. You may have many candidate keys. But you must choose one primary key. The primary key gets enforced by the database engine. It also becomes the reference for foreign keys. The other candidate keys stay as alternate keys. They remain valid for uniqueness checks. Choosing the primary key involves more than technical fit. You should pick one that is stable and simple. My advice: pick an ID-style primary key when natural keys are weak. This keeps data safe and queries fast.
Examples of Candidate Keys
Real examples make things clear. In an employee table, EmployeeID is a candidate key in DBMS. SocialSecurityNumber might also be a candidate key. In a book table, ISBN is a candidate key in DBMS. In a course table, a composite of CourseCode and Term can be a candidate key. Composite keys use more than one attribute. In a user table, Email can be a candidate key. But email can change. So choose wisely. I once used PhoneNumber as a key. It caused trouble when numbers changed. These examples show how practical needs shape candidate key in DBMS choices.
How to Find Candidate Keys (Step-by-Step)
Finding candidate keys is a logical process. First, list all attributes of the relation. Next, gather all known functional dependencies. Then, test attribute sets for closure. Compute the attribute closure for a set. If closure gives all attributes, the set is a superkey. Check minimality by removing attributes. If no proper subset is a superkey, it is a candidate key. Repeat until you find all minimal superkeys. Use this method to discover candidate key in DBMS for any schema. In practice, draw the dependencies. This visual step helps. I used it in a project and it cut design time.
Candidate Keys and Functional Dependency
Functional dependencies link attributes. They are critical to find candidate keys. A functional dependency says A → B. That means A determines B. If a set of attributes determines all others, it forms a superkey. Candidate keys follow from minimal superkeys. When you know dependencies, you can compute closures. This gives candidate key in DBMS choices. Keep a clear list of FDs while designing. I once missed an FD and picked a weak key. The database later showed duplicates. Checking dependencies first prevents such errors. Dependencies make candidate keys trustworthy and logical.
Composite Candidate Keys
A composite candidate key combines multiple attributes. Use it when one attribute cannot uniquely identify rows. For example, a class roster might use {StudentID, CourseID} as a composite key. Composite keys are valid candidate keys in DBMS. They can cause longer indexes though. They also affect foreign key design. You will need to reference the full composite key in other tables. Sometimes a surrogate primary key simplifies relationships. But composite keys express natural uniqueness. Choose composite candidate keys when natural uniqueness spans several attributes. I prefer them when data naturally demands it.
Candidate Keys in Normalization
Normalization reduces redundancy and avoids update anomalies. Candidate keys play a key role in normalization. In 1NF, you need a clear key for each relation. In 2NF and 3NF, candidate key dependencies guide decomposition. Partial dependencies on part of a composite key signal problems. Transitive dependencies also link back to keys. If a non-key attribute depends on another non-key attribute, normalize further. Using candidate key in DBMS well helps reach clean normal forms. I always map dependencies and keys when normalizing. This method makes sure tables are stable and consistent.
Implementing Candidate Keys in SQL
You enforce candidate keys in SQL with constraints. A PRIMARY KEY enforces one chosen candidate key. UNIQUE constraints help enforce other candidate keys. For composite candidate keys, list multiple columns in the constraint. Example: UNIQUE (email) or PRIMARY KEY (order_id, item_id). Use indexes to speed lookups on candidate keys. For surrogate keys, use SERIAL or AUTO_INCREMENT. In many systems, you still add UNIQUE constraints for natural candidate keys. This prevents accidental duplicates. When I design schemas, I always add UNIQUE constraints for alternate candidate keys to keep data safe.
Surrogate vs Natural Candidate Keys
Natural keys are real-world attributes. Surrogate keys are system-generated values. A candidate key in DBMS may be natural or surrogate. Natural keys can be meaningful. Surrogates are stable and compact. Surrogates avoid issues when real-world values change. But they hide semantic meaning. If you need readable identifiers, natural keys help. My rule: use surrogate primary key for flexibility. Keep natural candidate keys as UNIQUE constraints. This gives both stability and meaning. Use the approach that fits your project needs.
Common Mistakes with Candidate Keys
People make avoidable mistakes with candidate keys. They choose attributes that change often. They forget to check minimality. They confuse superkeys with candidate keys. They use long composite keys without reason. They do not add UNIQUE constraints for alternate keys. Another common error: assuming a set of attributes is unique without testing dependencies. These mistakes cause duplicates and broken relations. I once migrated a system and found three candidate keys missing constraints. Fixing those errors prevented future data corruption. Learn from such pitfalls and validate candidate key in DBMS choices early.
Tips for Choosing Good Candidate Keys
Pick keys that are stable over time. Prefer short and simple attributes. Avoid personal data like phone numbers when possible. Consider privacy and regulatory constraints. Test uniqueness on real data samples. Document your reasoning for choosing keys. Add UNIQUE constraints for alternate candidate keys. Think about joins and foreign keys when designing keys. If in doubt, use a surrogate primary key. Keep natural candidate keys as alternates. My practical tip: run queries to detect near-duplicates before finalizing keys. These steps make your design resilient and clear.
Frequently Asked Questions (FAQs)
Q1: How many candidate keys can a relation have?
A relation may have multiple candidate keys in DBMS. There is no strict limit. Each minimal unique attribute set counts. Some relations have one candidate key. Others have several. For example, a person table can have SSN and PassportNumber. Both are candidate keys. But you choose one as the primary key. The rest are alternate candidate keys. Having multiple keys is normal. Just enforce them with UNIQUE constraints. Testing helps find all candidate keys. Use functional dependencies to be sure.
Q2: Can a candidate key be composite?
Yes, a composite candidate key in DBMS combines attributes. If two or more attributes together identify rows, they form a composite key. Composite keys are common in join tables. They represent real-world uniqueness. But they require care when used as foreign keys. Often, designers use a surrogate primary key instead. Still, composite candidate keys are valid and useful. Choose them when natural uniqueness spans many attributes.
Q3: Are candidate keys always visible to users?
Not always. A candidate key in DBMS can be invisible to users. Surrogate keys often are hidden. Natural candidate keys like email are visible. Visibility depends on design choices. Visibility influences UX and security too. If you need readable IDs, choose natural keys. If you need stable IDs, choose surrogates. Balance these needs according to your application.
Q4: How do candidate keys affect query performance?
Candidate keys in DBMS often lead to indexes. Indexes speed up searches and joins. Primary keys usually have clustered indexes by default. UNIQUE constraints also create indexes. Well-chosen keys improve lookup speed. Large composite keys can slow down index operations. Keep keys compact for best performance. Monitor query plans to confirm index use. My experience: small integer keys deliver the best performance for heavy workloads.
Q5: Can candidate keys contain NULL values?
No. Candidate keys must not contain NULL values. NULLs break uniqueness guarantees. Primary keys and UNIQUE constraints typically disallow NULLs. In composite keys, all parts must be non-NULL. If an attribute can be NULL, it is not suitable for a candidate key. Choose attributes that always have values. This ensures reliable identification of rows.
Q6: How do functional dependencies help find candidate keys?
Functional dependencies are the backbone of key discovery. They show which attributes determine others. To find candidate keys, compute closures using FDs. If an attribute set’s closure equals all attributes, it is a superkey. Test minimality by removing attributes. If it still determines all attributes, it is not minimal. This method finds candidate keys methodically. In practice, draw FDs and compute closures systematically. I used this approach to resolve complex schema questions in a past job.
Conclusion
Understanding candidate key in DBMS makes database design clearer and safer. Candidate keys keep data unique and support normalization. They help you design efficient queries and reliable relations. Use the step-by-step method to find candidate keys. Test keys with real data and functional dependencies. Choose stable and minimal attributes for the best results. Add UNIQUE constraints to protect alternate candidate keys. When needed, use surrogate primary keys and keep natural candidates documented. If you want, I can review a table schema for you. Share your attributes, and I will suggest candidate keys and design tips. Let’s make your database solid and easy to manage.